Copy multiple files via ssh and preserve permissions and ownership. Creating a tarball on the fly and pipe its output through ssh afterwards extracting the files from the tarball will let us speedup the uploading times because the stream of data is continuous through the network and therefore will be done in one single connection. […]
Tag: ssh
SSH as SOCKs 5 proxy
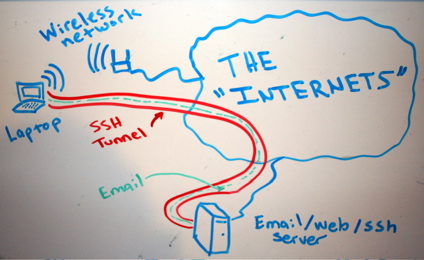
Let’s say, for example, that “someone” is traffic shaping our peer 2 peer connections or eavesdropping traffic in general, blocking myfavoritesite.net or any other domain/service… Here’s a really cool antidote: SSH proxy. I think it’s a really nice gesture to give someone the access on something that’s been blocked without his permission. To use ssh […]
Linux user account with ssh-only permissions
SSH (among other things) is a secure way of proxy-ing your traffic, web browsing or accessing a service remotely which is blocked by a firewall. In case we want someone else to have that access or securely proxying his traffic etc etc, we need to provide a user account with ssh-only access to our ssh […]
How to setup SSH – Install SSH server and client
What is SSH? Secure Shell or SSH is a network protocol that allows data to be exchanged using a secure channel between two networked devices. SSH was designed as a replacement for Telnet and other insecure remote shells, which send information, notably passwords, in plaintext, rendering them susceptible to packet analysis. The encryption used by […]
Linux Server Monitoring – Schedule a Command Output to be Sent via Email on Boot
Scheduling a command on boot it’s easy and it can be done with different ways. One, with cronjobs and second, with the rc.local file (/etc/rc.local). Third, by putting your own script in /etc/init.d/. Fow now I’ll take the easy way to do it, the one with the rc.local. Requirements: sSMTP Mutt email client Implementation Open […]
Disable Direct Root Logins
|
1 2 3 4 5 |
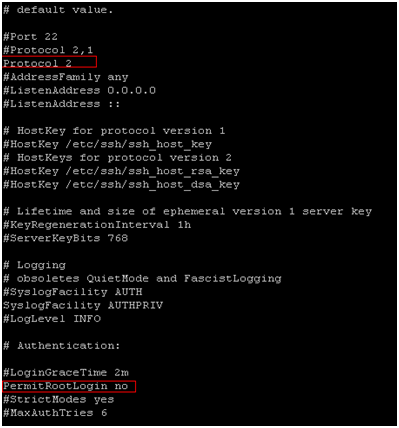
By disabling direct root logins on ssh helps you keep your server safer. Also you can manage to push ssh version 2. 1. <a title="How to setup SSH – Install SSH server and client" href="https://totallynoob.comhow-to-setup-ssh-install-ssh-server-and-client/" target="_blank">SSH</a> into your server and type <kbd>sudo su</kbd>to gain root previleges 2. [crayon-67179473cb94e889528323 lang="bash" ]nano /etc/ssh/sshd_config |
3. In nano type Ctrl+w to search for “protocol 2” and hit Enter 4. Uncomment and change it to look like Protocol 2 5.find the line PermitRootLogin yes 6. Uncomment it (if it’s commented) and make it look like PermitRootLogin no 7. Save the file and quit ( Ctrl+x -> y -> Enter) 8. […]