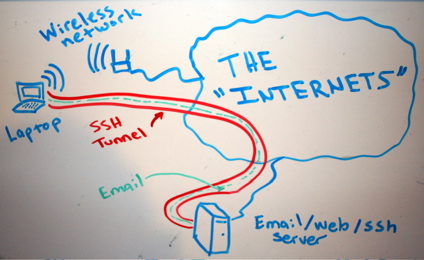
Let’s say, for example, that “someone” is traffic shaping our peer 2 peer connections or eavesdropping traffic in general, blocking myfavoritesite.net or any other domain/service… Here’s a really cool antidote: SSH proxy. I think it’s a really nice gesture to give someone the access on something that’s been blocked without his permission. To use ssh […]
Category: Privacy
Everything related to privacy, including data, audio/video communication
Linux user account with ssh-only permissions
SSH (among other things) is a secure way of proxy-ing your traffic, web browsing or accessing a service remotely which is blocked by a firewall. In case we want someone else to have that access or securely proxying his traffic etc etc, we need to provide a user account with ssh-only access to our ssh […]
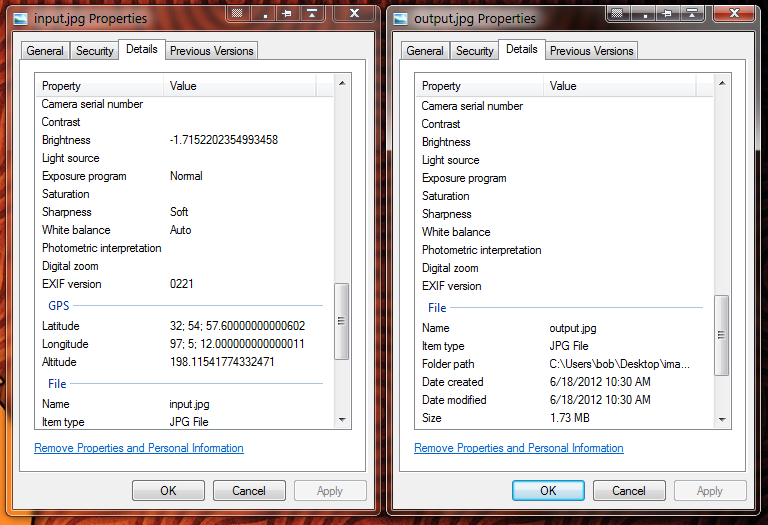
Delete your personal info from your photos with Exif tool
When you create an image, take a screenshot, take a picture with your smartphone or your computer etc, that picture is tagged with some metadata which can be used to track your location or your identity. In which file types are these metadata applied? Image files (scanned documents too), audio files. What info are embeded in photos? […]
Linux home directory encryption
Encrypting the $HOME directory under ubuntu/debian and other dists. In my case my $USER is “ubuntu” so be careful to replace that with your own user. Be sure to have more than the double free space in your $HOME than the size of the files to complete the migration, else copy your files temporarily in […]