What is SSH? Secure Shell or SSH is a network protocol that allows data to be exchanged using a secure channel between two networked devices. SSH was designed as a replacement for Telnet and other insecure remote shells, which send information, notably passwords, in plaintext, rendering them susceptible to packet analysis. The encryption used by […]
Series: SSH Best Practices
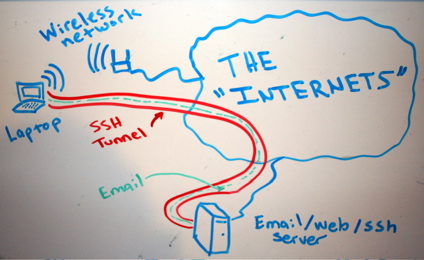
SSH tunneling, socks proxing, tips, tricks
SSH as SOCKs 5 proxy
Let’s say, for example, that “someone” is traffic shaping our peer 2 peer connections or eavesdropping traffic in general, blocking myfavoritesite.net or any other domain/service… Here’s a really cool antidote: SSH proxy. I think it’s a really nice gesture to give someone the access on something that’s been blocked without his permission. To use ssh […]
Linux user account with ssh-only permissions
SSH (among other things) is a secure way of proxy-ing your traffic, web browsing or accessing a service remotely which is blocked by a firewall. In case we want someone else to have that access or securely proxying his traffic etc etc, we need to provide a user account with ssh-only access to our ssh […]