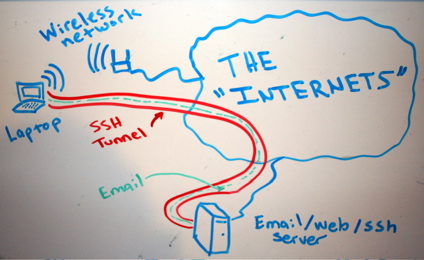
Let’s say, for example, that “someone” is traffic shaping our peer 2 peer connections or eavesdropping traffic in general, blocking myfavoritesite.net or any other domain/service… Here’s a really cool antidote: SSH proxy. I think it’s a really nice gesture to give someone the access on something that’s been blocked without his permission. To use ssh […]
Category: Security
Linux user account with ssh-only permissions
SSH (among other things) is a secure way of proxy-ing your traffic, web browsing or accessing a service remotely which is blocked by a firewall. In case we want someone else to have that access or securely proxying his traffic etc etc, we need to provide a user account with ssh-only access to our ssh […]
Linux home directory encryption
Encrypting the $HOME directory under ubuntu/debian and other dists. In my case my $USER is “ubuntu” so be careful to replace that with your own user. Be sure to have more than the double free space in your $HOME than the size of the files to complete the migration, else copy your files temporarily in […]
Disable Direct Root Logins
|
1 2 3 4 5 |
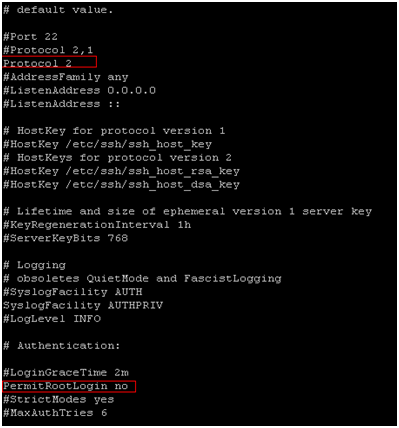
By disabling direct root logins on ssh helps you keep your server safer. Also you can manage to push ssh version 2. 1. <a title="How to setup SSH – Install SSH server and client" href="https://totallynoob.comhow-to-setup-ssh-install-ssh-server-and-client/" target="_blank">SSH</a> into your server and type <kbd>sudo su</kbd>to gain root previleges 2. [crayon-678ef9efa40ae852635908 lang="bash" ]nano /etc/ssh/sshd_config |
3. In nano type Ctrl+w to search for “protocol 2” and hit Enter 4. Uncomment and change it to look like Protocol 2 5.find the line PermitRootLogin yes 6. Uncomment it (if it’s commented) and make it look like PermitRootLogin no 7. Save the file and quit ( Ctrl+x -> y -> Enter) 8. […]