Let’s say, for example, that “someone” is traffic shaping our peer 2 peer connections or eavesdropping traffic in general, blocking myfavoritesite.net or any other domain/service… Here’s a really cool antidote: SSH proxy. I think it’s a really nice gesture to give someone the access on something that’s been blocked without his permission.
To use ssh as a proxy you need to set up first The ssh server on the server machine and the ssh client on you desktop (if it’s not already installed).
Create the tunnel
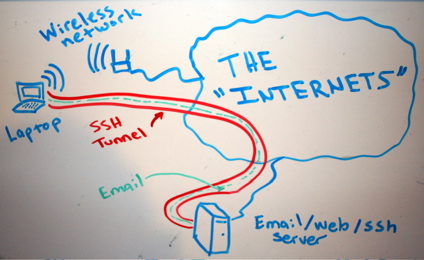
We need an encrypted tunnel from our client and all the way to the server so no one can spy our actions between this segment. We’re going to target our traffic to a local port, on the local machine, and the data will be “guided” to the server and the server will forward this traffic to the open internet. The segment between our server and the internet is unencrypted of course.
through terminal
Run the command below to your terminal. Assuming that your ssh server runs on port 22(which is a bad idea :P ) …
|
1 |
ssh -C2qTnN -D 8080 username@remote_machine.com |
or for a non default port use -p port
|
1 |
ssh -C2qTnN -D 8080 username@remote_machine.com -p 98756 |
Options explained:
- C = Compression
- 2 = Ssh version 2 only
- q = Quite mode, no messages will prompt the user
- T = Disable pseudo-tty allocation.
- n = Prevents reading from stdin. (Because it will run on the background).
- N = Do not execute remote command.
- D = “dynamic” application-level port forwarding so ssh can act as SOCKS server.
- -p = defines ssh’s server port.
through GUI
For GUI there is an ssh tunnel manager named gSTM follow the instructions below to install and configure.
1. Install it.
|
1 |
sudo apt-get install gstm |
2Run it. (Internet->gSTM)
3. Add new tunnel.

4. Configure new tunnel.

5. Start the new tunnel from the main screen.
Note: you will be prompted for user password.
Configure Firefox
- Open FF
- Install addon named “proxy selector”
- Go to Tools->Proxy Selector-> Manage Proxies->Add
- give it a name myTunnel
- hostname for SOCKs = localhost
- port for SOCKs = the local port we forwarded with ssh to the server
- open new tab and write to the address bar “about:config” (and say to FF that you’re a good boy)
- find “network.proxy.socks_remote_dns=FALSE” and set it to TRUE (thnx to @4li3n)




1 thought on “SSH as SOCKs 5 proxy”