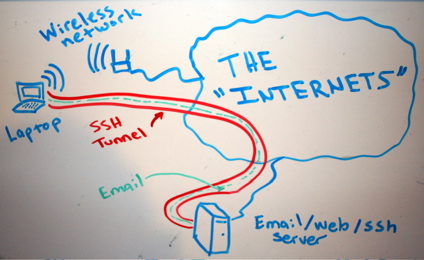
Let’s say, for example, that “someone” is traffic shaping our peer 2 peer connections or eavesdropping traffic in general, blocking myfavoritesite.net or any other domain/service… Here’s a really cool antidote: SSH proxy. I think it’s a really nice gesture to give someone the access on something that’s been blocked without his permission. To use ssh […]